By Maxim Integrated 90
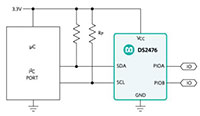
Maxim's DS2476Q+U is a secure, ECDSA and HMAC, SHA-256 coprocessor companion to the DS28C36Q+U. The coprocessor can compute any required HMACs or ECDSA signatures to do any operation on the DS28C36Q+U. The DS2476Q+U provides a core set of cryptographic tools derived from integrated, asymmetric (ECC-P256) and symmetric (SHA-256) security functions. In addition to the security services provided by the hardware-implemented crypto engines, the device integrates a FIPS/NIST true random number generator (RNG), 8 Kb of secured EEPROM, a decrement-only counter, two pins of configurable GPIO, and a unique 64-bit ROM identification number (ROM ID).
The ECC public and private key capabilities operate from the NIST-defined, P-256 curve and include FIPS-186-compliant ECDSA signature generation and verification to support a bidirectional, asymmetric key authentication model. The SHA-256's secret-key capabilities are compliant with FIPS 180 and are flexibly used either in conjunction with ECDSA operations or independently for multiple HMAC functions.
Two general-purpose input/output (GPIO) pins can be independently operated under command control and include configurability supporting authenticated and non-authenticated operation, including an ECDSA-based, crypto-robust mode to support secure-boot of a host processor. This secure-boot method can also be used to enable the coprocessor functions.
DeepCover® embedded security solutions cloak sensitive data under multiple layers of advanced security to provide the most secure key storage possible. To protect against device-level security attacks, invasive and noninvasive countermeasures are implemented including an active die shield, encrypted storage of keys, and algorithmic methods.
How Unclonable, Turnkey Embedded Security Protects Designs from the Ground Up
Isolate Software Execution with a DeepCover Security Framework
DeepCover Embedded Security Solution Guide
| Features | ||
|
|
| Applications | ||
|
|